As it is super bowl week / end, we thought we’d conjure up our best version of the classic ‘You Make the Call’ segments that appeared on Monday Night Football.
A recent article posted on ZDNet highlights research from Cisco’s 2014 Annual Security report.
In this report, Cisco (Sourcefire) highlights the fact that 91% of all web exploits are related to Java. Not to be out done, Cisco’s TRAC/SIO group claims different results within the same report; for those of us not familiar with that acronym. TRAC/SIO stands for Threat Research Analysis and Communications & Security Intelligence Operations group. TRAC/SIO found that Java malware encounters peaked at just 14 percent in April, compared to “all web malware”.
To be fair, Sourcefire has restricted its range of web exploits to Java; Microsoft Word, Excel, and PowerPoint; and Adobe Reader whereas TRAC/SIO has expanded their horizon to various other types of exploits.
Not to be outdone, AV-Test reported back in in December that Java, Adobe Reader and Adobe Flash have been responsible for 66% of the vulnerabilities exploited by malware on Windows platforms since the year 2000.
What’s does iScan Online See?
Well, we can tell you from working with our clients that about 60% of the Windows desktop and laptop computers scanned for vulnerabilities using iScan Online the majority of the vulnerabilities identified on those systems are attributed to Adobe and Java.
Why do these vulnerabilities go unpatched?
It’s pretty simple. At iScan Online, we are able to scan the “Dark matter” of your network. Those devices that traditional management and vulnerability scanning solutions cant assess. These devices are BYOD, used by road warriors, remote workers home workers and may never actually attach directly to your corporate network but they will interact with your applications and data via VPN, web apps and more.
If you rely on users of these devices to update and patch their own systems, they don’t know that all apps aren’t automatically updated via Microsoft Windows Update and will run update for Adobe flash but not know that they need to run updates for all other Adobe products.
Whats The Risk?
So what does this all mean? Why should I care about patching these vulnerabilities? The reality is we all have trusted access and store sensitive data. Regardless if we are interacting with web applications on a laptop, syncing files from location to location or connecting via VPN. The end result is our unpatched laptops and mobile devices are the perfect launch point for criminals to gain access to sensitive data regardless of whether the data is stored locally on the device or these devices are used as a malware launch point after compromising them through an unpatched Adobe or Java vulnerability.
You make the call.
If you are interested in seeing how to engage your user community in the security conversation that will help reduce the amount of exploits and data loss in all platforms, check out iScan Online’s simplified security report that gives users helpful information about how to resolve the issues with Java, Adobe and other apps installed on their devices.
View a sample security report: https://www.iscanonline.com/page/vuln-report



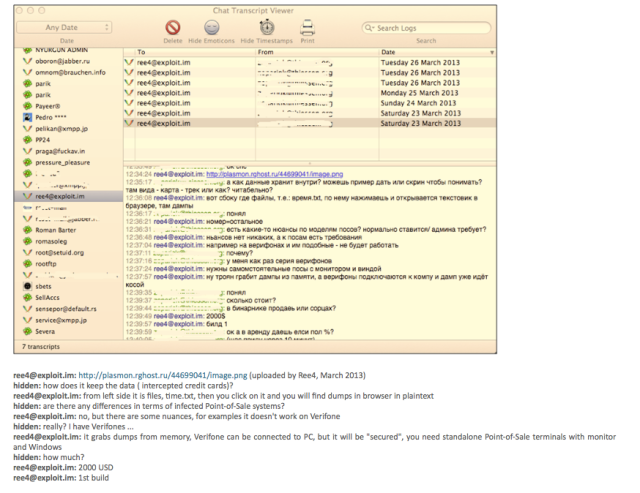
 When the topic of data breach comes up, encryption and vulnerability scanning are usually part of the solution. But most people don’t realize that getting a frequent assessment on all endpoints can be just as important as securing the payment processing gateway. In fact, many experts consider cardholder data discovery the “third pillar” for overall data breach mitigation.
When the topic of data breach comes up, encryption and vulnerability scanning are usually part of the solution. But most people don’t realize that getting a frequent assessment on all endpoints can be just as important as securing the payment processing gateway. In fact, many experts consider cardholder data discovery the “third pillar” for overall data breach mitigation.